All battles are won BEFORE they are ever fought. – Sun Tzu
The biggest problem facing blockchain today is scalability.
Take CryptoKitties. When the blockchain-based collectable cats were introduced in October 2017, they were all the rage. Thousands of cats were created and sold, with some kitties fetching prices of over $100,000. CryptoKitties was built on the Ethereum network, which couldn’t handle the load. CryptoKitties crashed Ethereum.
Rule of thumb: whenever a blockchain application gets popular, the blockchain breaks.
This is due to the primitive state of consensus algorithms—the method that lets all the nodes on a blockchain network agree with each other. Each consensus algorithm has its own set of limitations and flaws:
| Consensus Algorithm | Used by | Limitation/Flaw |
|---|---|---|
| Proof of Work | Bitcoin, Ethereum | Energy Consumption |
| Proof of Stake | EOS | Unbalanced/Inherent Inequality |
| Tangle | IOTA | Centralized Coordinator |
| Swirlds | In development | Proprietary, limits innovation |
| Delegated Proof of Stake | Lisk | Trades decentralization for speed and scalability |
We’ve been working with our client Cyberspec to develop Proof of Selection, a new consensus algorithm that is:
- less resource-intensive than Proof of Work
- more balanced than Proof of Stake
- without a centralized coordinating process (e.g., Tangle Coordinator)
- not proprietary (e.g., Swirlds)
- fast and scalable without sacrificing centralization (e.g., DPOS)
In this post, we’ll:
- Show how Proof of Selection does not require mining, has equal block publishing rights that are not based on stake, and has no centralized coordinating processes.
- Outline a new digital ledger infrastructure based on Proof of Selection to achieve a more efficient method of decentralized currency, storage, data transactions, and research.
- Explain how to integrate Proof of Selection into existing digital ledger technologies that need better scaling or more decentralization.
This is how Proof of Selection will solve the blockchain scalability problem.
The Proof of Selection Story
Water adapts its course according to the terrain; in the same way, you should shape your victory around the enemy’s dispositions. – Sun Tzu
Officer Kennie Jenkins of the United States Navy had a problem. It was such a famous problem that it had a name: the Byzantine General’s Dilemma.
Imagine an army of generals are encircled around an ancient city. They need a way to coordinate the attack on the city, since a half-hearted attack will result in defeat. It’s ancient times, so communication is poor. There may also be traitors in their midst who are sending false messages.
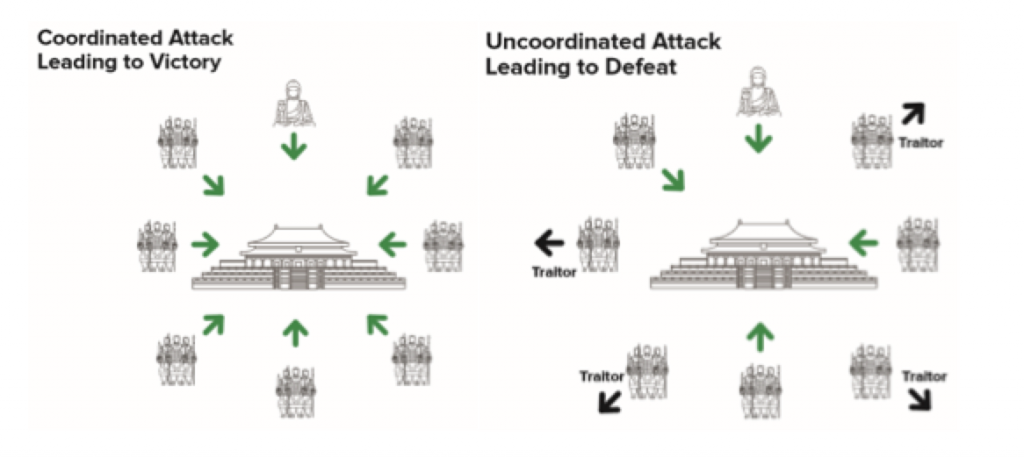
The Byzantine General’s Dilemma is this: How can multiple generals agree on a plan of attack without the ability to reliably communicate with each other?
During a ten-year career with the United States Navy, Jenkins had earned a Master’s Degree in the field of cybersecurity, briefing personnel at the highest levels of the United States Military and Department of Defense. Ultimately this led to the founding of his own cybersecurity company, Cyberspec.
He saw the Byzantine General’s Dilemma was the same problem faced by blockchain: consensus mechanisms need a way to agree. Like the generals, communication between blockchain nodes is often poor, and traitors (in the form of hackers) may try to send false messages.
Applying his knowledge of military history, Jenkins understood that an imperfect plan that’s executed in a timely manner will be more effective than a perfect plan that is implemented too late; therefore, he immediately began implementing his vision for a fully-decentralized consensus algorithm that is resource efficient, fully transparent, and egalitarian.
He called this algorithm Proof of Selection.
How Proof of Selection Works
The General must be possessed of wisdom, honesty, benevolence, courage, and discipline. – Sun Tzu
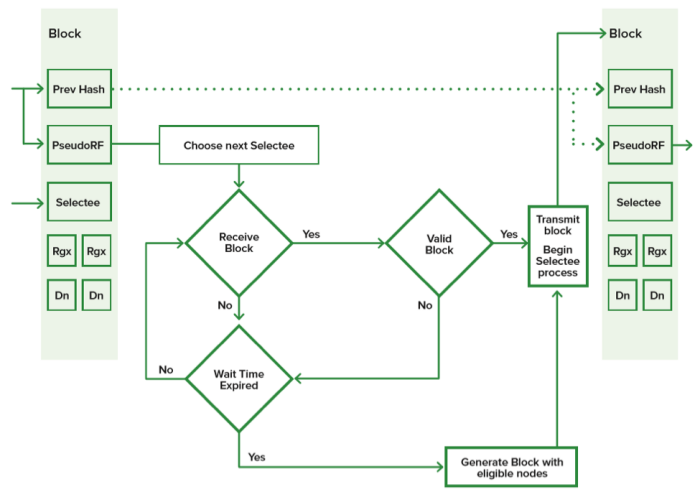
Cyberspec’s Proof of Selection algorithm works by developing consensus around “selecting” the next nodes to create a block in the blockchain. It’s like the Byzantine Generals coordinating a time to attack or retreat, as well as a method of detecting traitors in their midst.
It involves an agreement of:
- who is eligible to be selected (the eligible node);
- who is selected to build the next block (using the PseudoRF function).
 An eligible node is a node that has registered their public key into the chain by a digital signature and is still considered active. Nodes that have registered (Rgx) can then be selected by the pseudo-random function, PseudoRF—like selecting a random general’s name out of a hat.
An eligible node is a node that has registered their public key into the chain by a digital signature and is still considered active. Nodes that have registered (Rgx) can then be selected by the pseudo-random function, PseudoRF—like selecting a random general’s name out of a hat.
The PseudoRF will automatically select these node(s) to create the next block(s). This selection is determined by the previous block hash and block creation timestamp. Transactions are timestamped and monitored by the rest of the network; a block is valid only if the rest of the network agrees.
Along with eligible nodes, dead nodes (Dn) must be similarly identified. To register an eligible node, a simple function logging a node’s public key into the blockchain is used. To register a dead node, an invalid block or no response upon selection must occur. After an adjustable number of dead registrations occur, the node is considered dead and is removed from the selection process.
Why Proof of Selection is Better
Attack at points that the enemy must scramble to defend. – Sun Tzu
Existing consensus algorithms have plenty of problems. Proof of Selection provides the solution.
| Consensus Algorithm | Limitation/Flaw | Proof of Selection Solution |
|---|---|---|
| Proof of Work | Energy Consumption | No mining, no computer power imbalance |
| Proof of Stake | Unbalanced/Inherent Inequality | Equal Block Publishing Rights |
| Tangle | Centralized Coordinator | Fully Decentralized |
| Swirlds | Proprietary, limits innovation | Open Source, no transaction fees |
| Delegated Proof of Stake | Trades decentralization for speed and scalability | Fully decentralized / no stake |
Proof of Work (POW) is flawed, because nodes with the most power or pooled power can control the blocks created, transactions logged, monetary rewards, and ultimately the core of the program. Controlling any of these areas can skew the currency in a way that serves the purpose of the computers with the most power.
Proof of Work also consumes vast amounts of power. Mining proponents reason that as a store of value, performing work is a good way to ensure that the resulting coins will always have value; however, that fact does not justify the power usage. Further, the digital age is all about efficiency. While there will always be a place for cryptocurrency mining, the future will likely witness an inevitable move from mining digital currencies to more efficient methods.
Proof of Stake is the most common alternative: staking resources to have the right to create a block or write to the ledger. While this can be effective, ensuring that the stakes are not applied unequally requires various methods to offset the threat of centralization. In general, they require using a value system or tokens to bet or invest on the valid blocks. Some implementations entirely remove mining, but in some cases, the weighted dynamic creates a volatile environment that is not ideal for an equally distributed system.
Tangle Coordinator (IOTA) is a consensus method that removes mining and integrates with a digital ledger technology called the Directed Acyclic Graph (DAG). However, there is a central coordinator who provides rudimentary functions to validate the new blocks at regular intervals. Tangle also requires some POW prior to accepting a new block.
The Swirlds (Hashgraph) methodology also removes mining and is used in conjunction with DAG, but the primary negative issue is that it is proprietary software and not open source, limiting its full technological review and potential for innovation. Further, participants not running nodes can influence consensus with their stake; essentially Swirlds uses a modified proof of stake methodology.
Delegated Proof of Stake (DPOS) is a technology that offers advantages in terms of speed and scalability, but at the expense of decentralization. DPOS requires a subset of nodes to be granted publishing powers. First, that subset of nodes results in less decentralization. For example, some technologies, such as EOS, only use around 20 delegate nodes for their entire network. Second, the nodes that are voting for these delegates are essentially paying assets to stake the delegates. This means that any organization could ensure delegate nodes remain in power with funding, which again, results in less decentralization.
Proponents of DPOS state that the small sacrifice in centralization is acceptable for the gains in scalability; however, that cost could prove to be extremely detrimental, and is therefore, difficult to quantify. For example, a typical DPOS technology could create the illusion of decentralization in that delegate nodes could be located all over the world; however, a single organization or country could be staking all of those nodes.
The New Digital Ledger
The ultimate achievement is to defeat the enemy without coming to battle. Change the flag and standard of the captured chariots, and add them to your own squadron. – Sun Tzu
Proof of Selection makes possible a new type of Digital Ledger that:
- Uses the Proof of Selection algorithm.
- Eliminates the requirement for an internal currency for applications (e.g., ether/gas).
- Improves registration and tagging of transactions so that nodes can ignore blocks or data not slated for their needs.
For example, a ledger such as Ethereum creates a dynamic that allows miners to ignore the lowest paying applications, thus creating a natural bias for high-paying apps. With no natural bias, all transaction rewards using Proof of Selection are equal. As a result, the resulting incentives include:
- Currency is issued at block creation (similar to bitcoin);
- Currency can rise in value on crypto exchanges;
- The application can attract more users at a lower cost;
- Application owners can pay nodes to host their application;
- Application owners retain the ability to have anyone else host the same decentralized application and data.
In order to take over a market with established players, blockchain projects using Proof of Selection do not need to directly confront the competition. In the same manner as a skilled general who can turn enemies into allies and utilize an enemy’s existing resources, developers are not limited to building new ledgers and attempting to establish them in the industry. They can build Proof of Selection into existing ledgers, or add its functionality on top of them.
Challenges and Solutions
A wise leader always considers both advantages and disadvantages equally – Sun Tzu
Although the potential of Proof of Selection is enormous, there are several challenges and issues that are still being researched. These include rewards, attacks, privacy, and Delegated Proof of Stake.
Who best understands the use of rewards and punishments? – Sun Tzu
The principle purpose of rewards is to promote nodes to stay online, send transactions, and process blocks. There is no competition mechanism built into Proof of Selection; if a node is selected, a reward is issued—one Sel will represent the reward for the creation of a block.
 The actual value of a Sel will be sorted by the market; however, the ratio between created blocks to active nodes could create an environment where nodes have limited natural incentive to be a part of the network.
The actual value of a Sel will be sorted by the market; however, the ratio between created blocks to active nodes could create an environment where nodes have limited natural incentive to be a part of the network.
In an attempt to ensure a built-in incentive for all network users, a configuration will be available to reward active nodes at certain intervals for nodes that have not been selected within a certain timeframe. The opposite configuration will also be available—to not issue rewards if the number of blocks created vastly outnumbers the active nodes.
If you know yourself, and you know your opponent, you will be undefeated in 100 battles. – Sun Tzu
With any new consensus algorithms, the following potential attacks must be addressed: Double spending, forks, 51% attacks, Sybil attacks (fake nodes), selection fixing (specific to Proof of Selection). Proof of selection will:
- handle double-spending by discarding invalid blocks
- de-incentivize fake node creation
- prevent a Sybil attack from lasting long enough to acquire a significant number of Sels
When you find the enemy’s agents spying on you, offer them bribes. – Sun Tzu
Concerning privacy, the Proof of Selection infrastructure will be open—though privacy does not necessarily have to occur at the infrastructure level. Proof of Selection addresses the problems associated with Mixers and Zero-Knowledge proofs by eliminating transaction fees, eliminating mining, and adding the ability to selectively process applications.
In the conduct of war, the general receives his orders from the ruler; it is then the general’s job to marshal the forces available to him, put them into effective order, and build their encampment. After receiving his appointment as Commander, when the Commander is at the head of the army, he need not accept all of the ruler’s orders. – Sun Tzu
Proof of Selection aims to remove that centralization problem by eliminating the idea of stake, which is at the core of the DPOS centralization problem. Further, ensuring that every device can participate directly, and not via proxy, allows for a larger network that is critical to all trustless technologies.
Too Long; Didn’t Read
The essence of military operations is speed. – Sun Tzu
Proof of Selection is a revolutionary consensus algorithm that improves upon the limitations of existing consensus algorithms. It removes mining requirements and promotes equal block publishing and transaction rights without any centralized coordinating processes or authority.
Proof of Selection is fast, with no time restrictions on block creation, and it is also scalable due to its ability to increase the number of selected nodes. The Proof of Selection consensus algorithm can potentially revolutionize digital ledgers and become the world standard for blockchain.
Download the Cyberspec Battle Plan here
